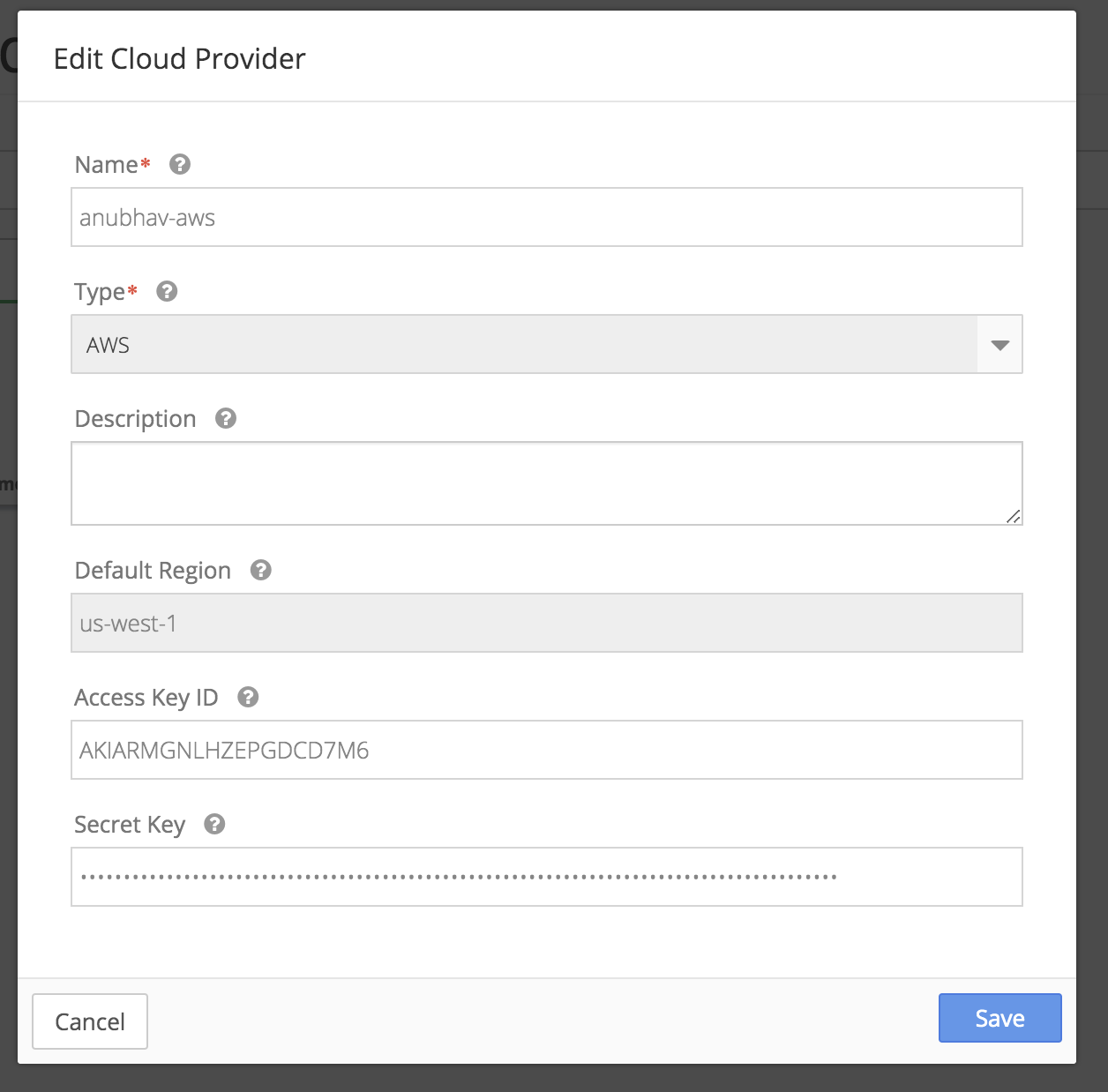
For using AWS access using AWS User configuration, you must create a new user with necessary policy access and then use the user access credentials (access key ID and secret access key) for cloud provider integration authentication. You need create a policy with specific permissions for the User.
To create a new user for Nirmata Private Edition:
- Login to the AWS Management Console and select IAM Services.
- Under Identity and Access Management (IAM) > Policies, click Create Policy.
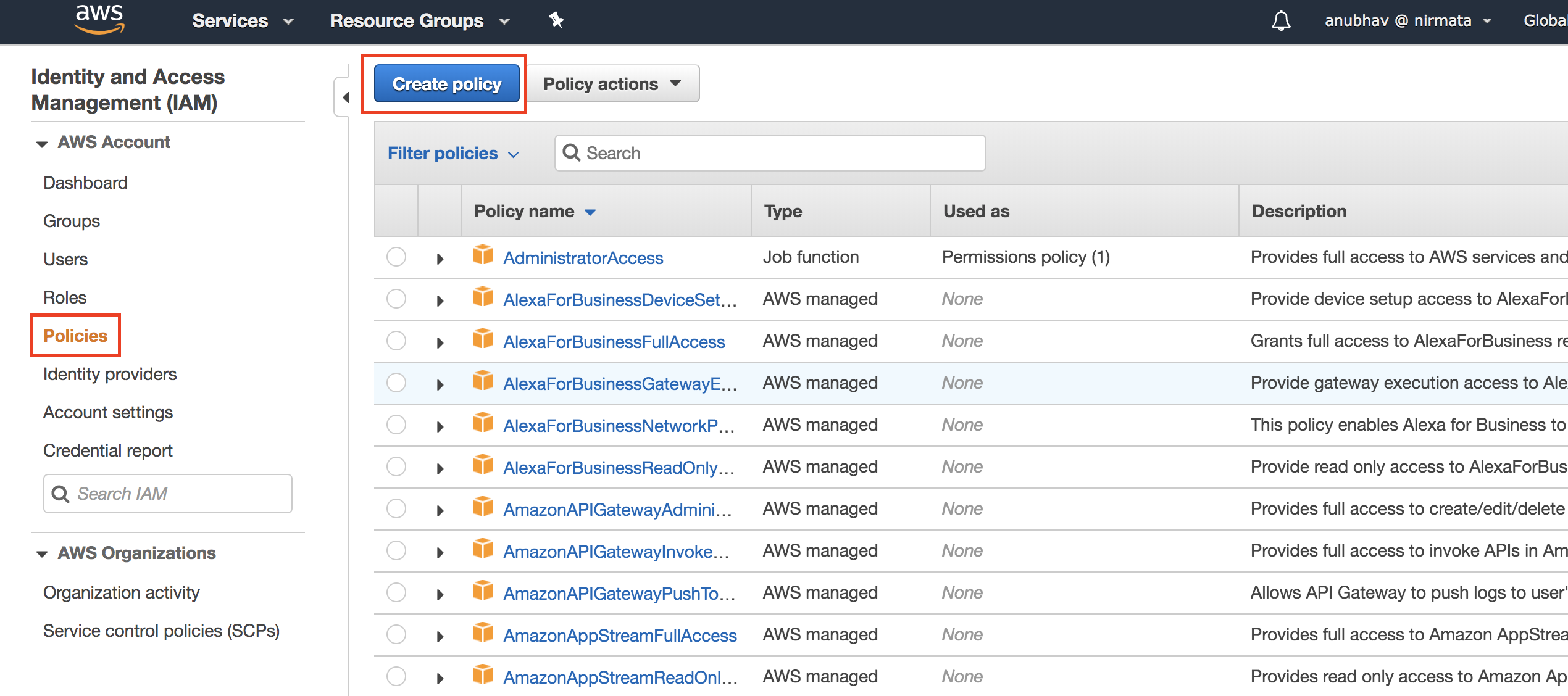
- Under Policy, choose JSON and copy-paste the permissions as highlighted below -
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"ec2:TerminateInstances",
"ec2:StartInstances",
"ec2:StopInstances"
],
"Resource": "arn:aws:ec2:*:094919933512:instance/*",
"Condition": {
"StringEquals": {
"ec2:ResourceTag/com.nirmata.createdBy": "nirmata"
}
}
},
{
"Sid": "VisualEditor1",
"Effect": "Allow",
"Action": [
"iam:GetPolicyVersion",
"autoscaling:Describe*",
"iam:ListInstanceProfilesForRole",
"iam:PassRole",
"iam:SimulateCustomPolicy",
"iam:ListAttachedRolePolicies",
"iam:ListAttachedUserPolicies",
"iam:ListAttachedGroupPolicies",
"iam:ListRolePolicies",
"iam:ListPolicies",
"iam:GetRole",
"iam:GetPolicy",
"iam:ListGroupPolicies",
"ec2:CreateTags",
"iam:ListRoles",
"ec2:RunInstances",
"iam:ListUserPolicies",
"iam:ListInstanceProfiles",
"ec2:Describe*",
"iam:ListPolicyVersions",
"iam:GetUserPolicy",
"iam:ListGroupsForUser",
"iam:ListUsers",
"iam:GetGroupPolicy",
"iam:GetUser",
"iam:GetRolePolicy",
"iam:GenerateCredentialReport",
"iam:GenerateServiceLastAccessedDetails",
"iam:Get*",
"iam:List*",
"iam:SimulateCustomPolicy",
"iam:SimulatePrincipalPolicy",
"iam:GetPolicyVersion",
"iam:SimulateCustomPolicy",
"iam:GenerateCredentialReport",
"iam:GenerateServiceLastAccessedDetails",
"iam:Get*",
"iam:List*",
"iam:SimulateCustomPolicy",
"iam:SimulatePrincipalPolicy",
"iam:CreateRole",
"iam:DeleteRole",
"iam:AttachRolePolicy",
"iam:DetachRolePolicy",
"iam:CreateInstanceProfile",
"iam:DeleteInstanceProfile",
"iam:AddRoleToInstanceProfile",
"iam:RemoveRoleFromInstanceProfile"
],
"Resource": "*"
},
{
"Sid": "VisualEditor2",
"Effect": "Allow",
"Action": [
"cloudformation:CreateStack",
"cloudformation:DeleteStack",
"cloudformation:CreateChangeSet",
"cloudformation:UpdateStack",
"cloudformation:ExecuteChangeSet",
"cloudformation:Describe*",
"cloudformation:EstimateTemplateCost",
"cloudformation:Get*",
"cloudformation:List*",
"cloudformation:ValidateTemplate",
"cloudformation:DetectStackDrift",
"cloudformation:DetectStackResourceDrift,
]
}
- Click Review Policy and save the policy.
You can now create a user required for EC2 instance management in Nirmata that will use this Policy.
To generate a AWS Access Key ID and Secret key:
- Login to the AWS Management Console and select IAM Services.
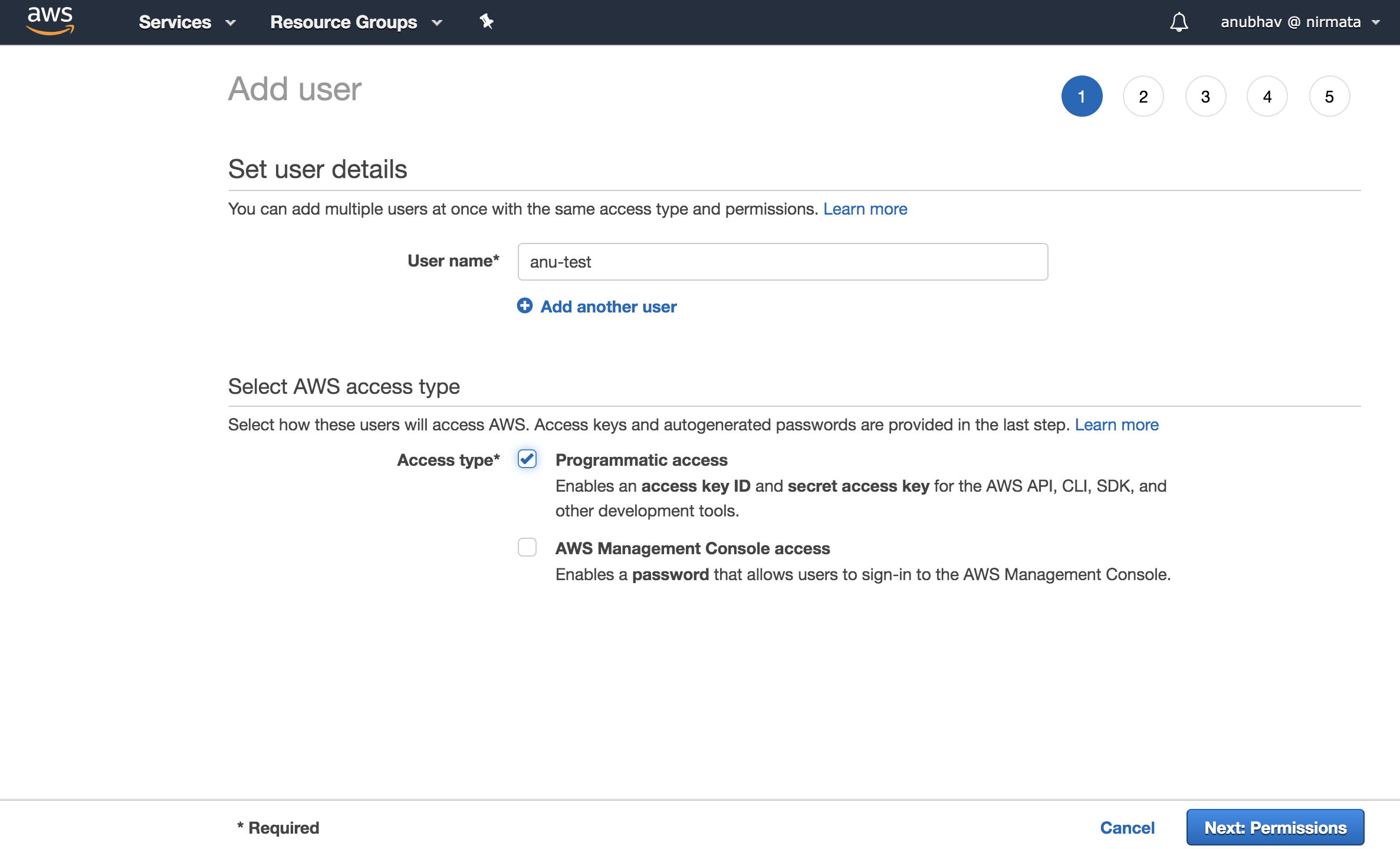
- Select Users and click Add a User.
- Select programmatic access and click Next:Permission.
- Choose Attach existing policies directly and select the policy you created above.
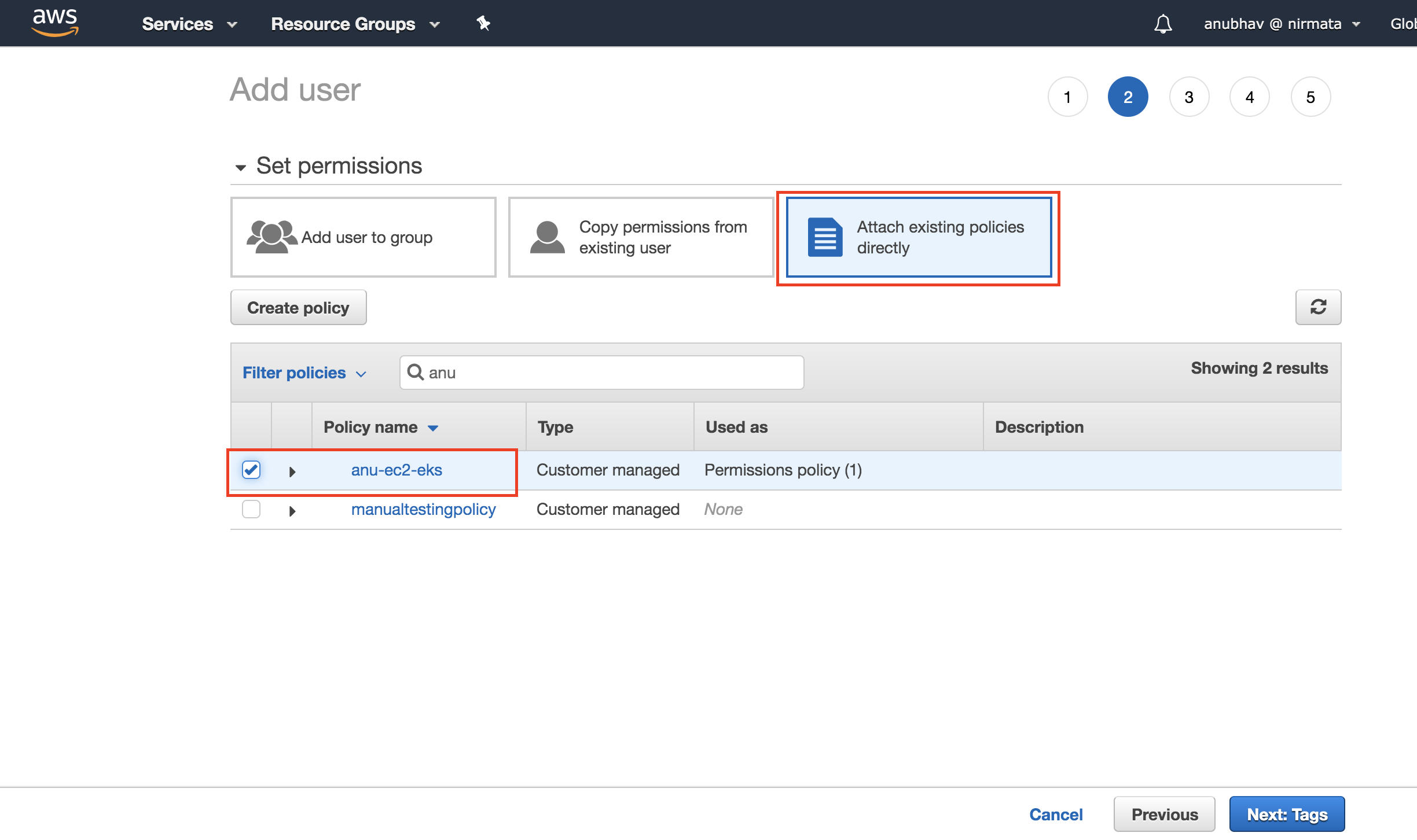
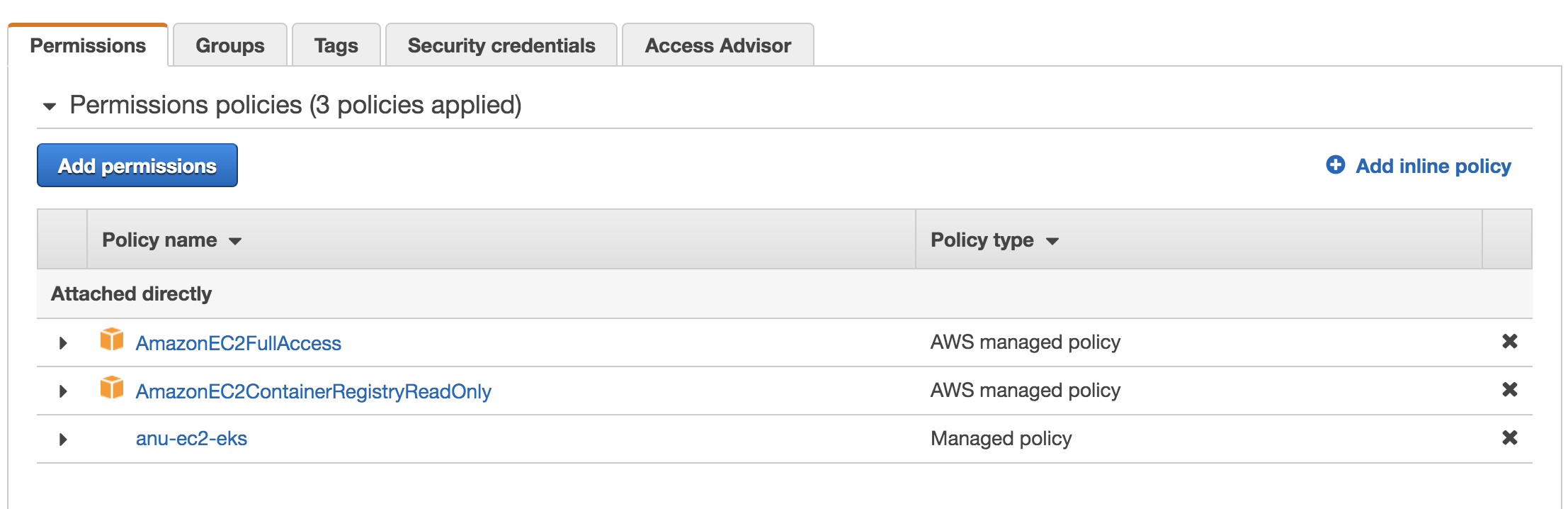
Add AWS Managed Policies such as AmazonEC2FullAccess and AmazonEC2ContainerRegistryReadOnly also .
-
Click Security Credentials tab on the User menu and click Create Access Key
-
Download the Access Key Id and secret key .
You can add the Access Key ID secret key in Nirmata.