To deploy the RBAC YAML to a cluster, open the cluster and then select Apply YAML from the Cluster Settings menu.
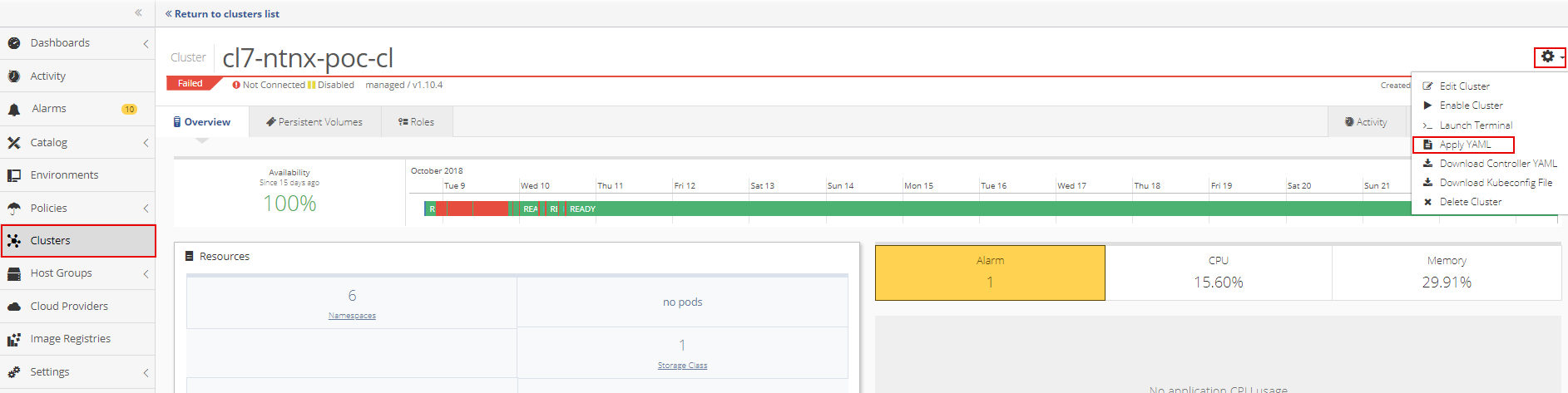
Drop the RBAC YAML file into the upload box or select the file from the directory.
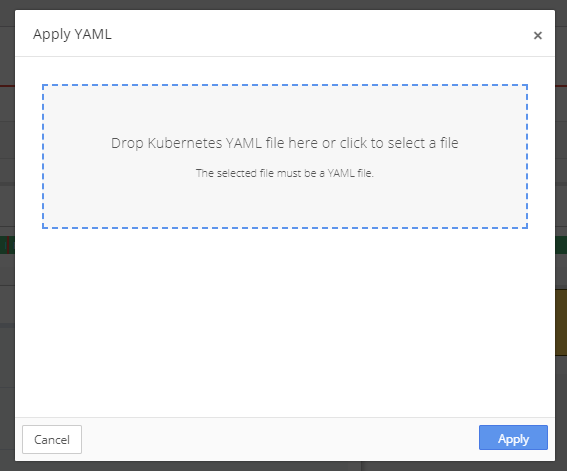
RBAC YAML:
---
apiVersion: v1
kind: ServiceAccount
metadata:
name: csi-attacher
namespace: kube-system
---
kind: ClusterRole
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: external-attacher-runner
namespace: kube-system
rules:
- apiGroups: [""]
resources: ["secrets"]
verbs: ["get", "list"]
- apiGroups: [""]
resources: ["events"]
verbs: ["get", "list", "watch", "update"]
- apiGroups: [""]
resources: ["persistentvolumes"]
verbs: ["get", "list", "watch", "update"]
- apiGroups: [""]
resources: ["nodes"]
verbs: ["get", "list", "watch"]
- apiGroups: ["storage.k8s.io"]
resources: ["volumeattachments"]
verbs: ["get", "list", "watch", "update"]
---
kind: ClusterRoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: csi-attacher-role
namespace: kube-system
subjects:
- kind: ServiceAccount
name: csi-attacher
namespace: kube-system
roleRef:
kind: ClusterRole
name: external-attacher-runner
apiGroup: rbac.authorization.k8s.io
---
# needed for StatefulSet
kind: Service
apiVersion: v1
metadata:
name: csi-attacher-ntnx-plugin
namespace: kube-system
labels:
app: csi-attacher-ntnx-plugin
spec:
selector:
app: csi-attacher-ntnx-plugin
ports:
- name: dummy
port: 12345
---
apiVersion: v1
kind: ServiceAccount
metadata:
name: csi-provisioner
namespace: kube-system
---
kind: ClusterRole
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: external-provisioner-runner
namespace: kube-system
rules:
- apiGroups: [""]
resources: ["secrets"]
verbs: ["get", "list"]
- apiGroups: [""]
resources: ["persistentvolumes"]
verbs: ["get", "list", "watch", "create", "delete"]
- apiGroups: [""]
resources: ["persistentvolumeclaims"]
verbs: ["get", "list", "watch", "update"]
- apiGroups: ["storage.k8s.io"]
resources: ["storageclasses"]
verbs: ["get", "list", "watch"]
- apiGroups: [""]
resources: ["events"]
verbs: ["list", "watch", "create", "update", "patch"]
---
kind: ClusterRoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: csi-provisioner-role
namespace: kube-system
subjects:
- kind: ServiceAccount
name: csi-provisioner
namespace: kube-system
roleRef:
kind: ClusterRole
name: external-provisioner-runner
apiGroup: rbac.authorization.k8s.io
---
# needed for StatefulSet
kind: Service
apiVersion: v1
metadata:
name: csi-provisioner-ntnx-plugin
namespace: kube-system
labels:
app: csi-provisioner-ntnx-plugin
spec:
selector:
app: csi-provisioner-ntnx-plugin
ports:
- name: dummy
port: 12345
---
apiVersion: v1
kind: ServiceAccount
metadata:
name: csi-ntnx-plugin
namespace: kube-system
---
kind: ClusterRole
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: csi-ntnx-plugin
namespace: kube-system
rules:
- apiGroups: [""]
resources: ["secrets"]
verbs: ["get", "list"]
- apiGroups: [""]
resources: ["nodes"]
verbs: ["get", "list", "update"]
- apiGroups: [""]
resources: ["namespaces"]
verbs: ["get", "list"]
- apiGroups: [""]
resources: ["persistentvolumes"]
verbs: ["get", "list", "watch", "update"]
- apiGroups: ["storage.k8s.io"]
resources: ["volumeattachments"]
verbs: ["get", "list", "watch", "update"]
---
kind: ClusterRoleBinding
apiVersion: rbac.authorization.k8s.io/v1
metadata:
name: csi-ntnx-plugin
namespace: kube-system
subjects:
- kind: ServiceAccount
name: csi-ntnx-plugin
namespace: kube-system
roleRef:
kind: ClusterRole
name: csi-ntnx-plugin
apiGroup: rbac.authorization.k8s.io